Proxy Mechanics
How Proxies Work
Proxies are a flexible gateway for your device's connection to every website. Without a proxy, websites send content back to your device's unique IP (Internet Protocol) address. With a proxy, websites only send content back to the proxy's IP address, which then forwards web content to your device:
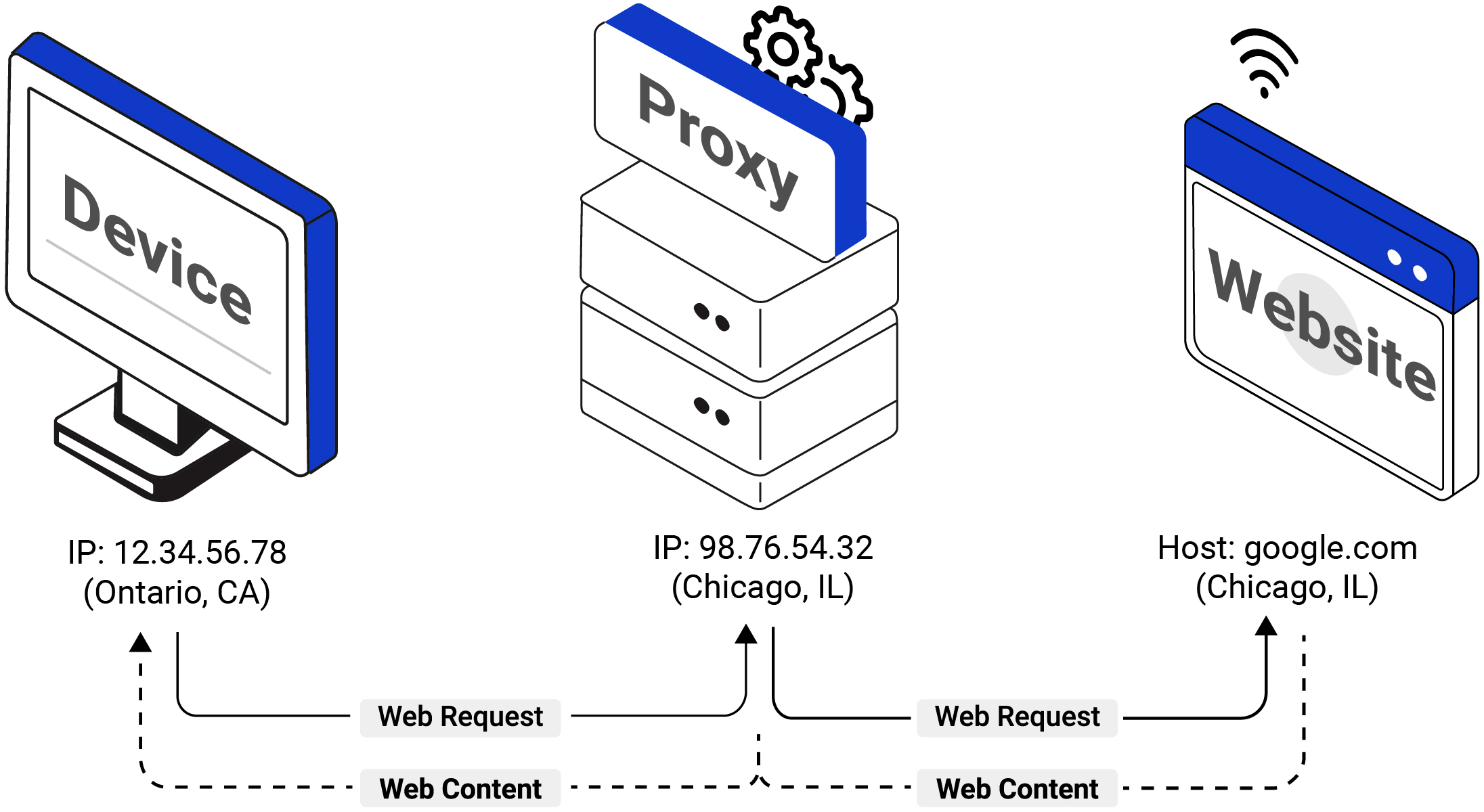
As illustrated above, in a proxied web request:
- Your browser (e.g., Chrome) can request websites through the proxy.
- Websites only see the proxy server's IP address for the incoming request.
- The proxy server then forwards the web content back to you.
What Websites Can Detect
Without a proxy, websites you access can see your unique internet protocol address (and the associated geolocation information), any data shared by your browser, and most critically – any data that can be linked to your IP and browsing "fingerprint" through various commercial & government databases that aggregate personal data – including IP fingerprints!
| IP Information (via HTTP connection) | Browser Information (shared by your browser) | Linked Data (in third-party databases) |
| IP City IP Zip IP Region IP Latitude IP Longitude IP Timezone ISP Name ISP Domain ISP Registered ASN Connection Latency Nearby Network Hops | Browser Type & Version Browser Website Cookies Browser Plugins & Extensions Operating System Type & Version Screen Resolution, Color Depth System Locale, Language, Timezone System Installed Fonts System CPU Class Canvas Fingerprinting WebGL Fingerprinting Audio Fingerprinting | Device IDs (if linked) Household Address (if linked) Names (if linked) Emails (if linked) Phones (if linked) Social Profiles (if linked) Browsing History (if linked) Purchase History (if linked) Property Records (if linked) Court Records (if linked) Vehicle Records (if linked) |
IP Address Geolocation Data
Your IP address is your device's unique identifier assigned by our Internet Service Provider (ISP) for connecting to the Internet.
For your request to this website (squidproxies.com), our web server sees:
From there, popular IP address databases typically share the following information about your IP:
| ISP Name | ... |
| IP City | ... |
| IP Region | ... |
| IP Country | ... |
| IP Coordinates | ... |
| Continent | ... |
| Timezone | ... |
| ISP Organization | ... |
https://ip.squidproxies.com
These popular geolocation services maintain independent IP location databases, so you can test your IP address against additional IP geolocation databases below:
Browser Fingerprint Data
Your browser also reveals a tremendous amount of information about your system to websites for applications to optimize your browsing experience. However, sophisticated data aggregators have combined each of these data points together into a "IP + browser fingerprint" which can often be used to uniquely identify your browser and device across all the websites you interact with.
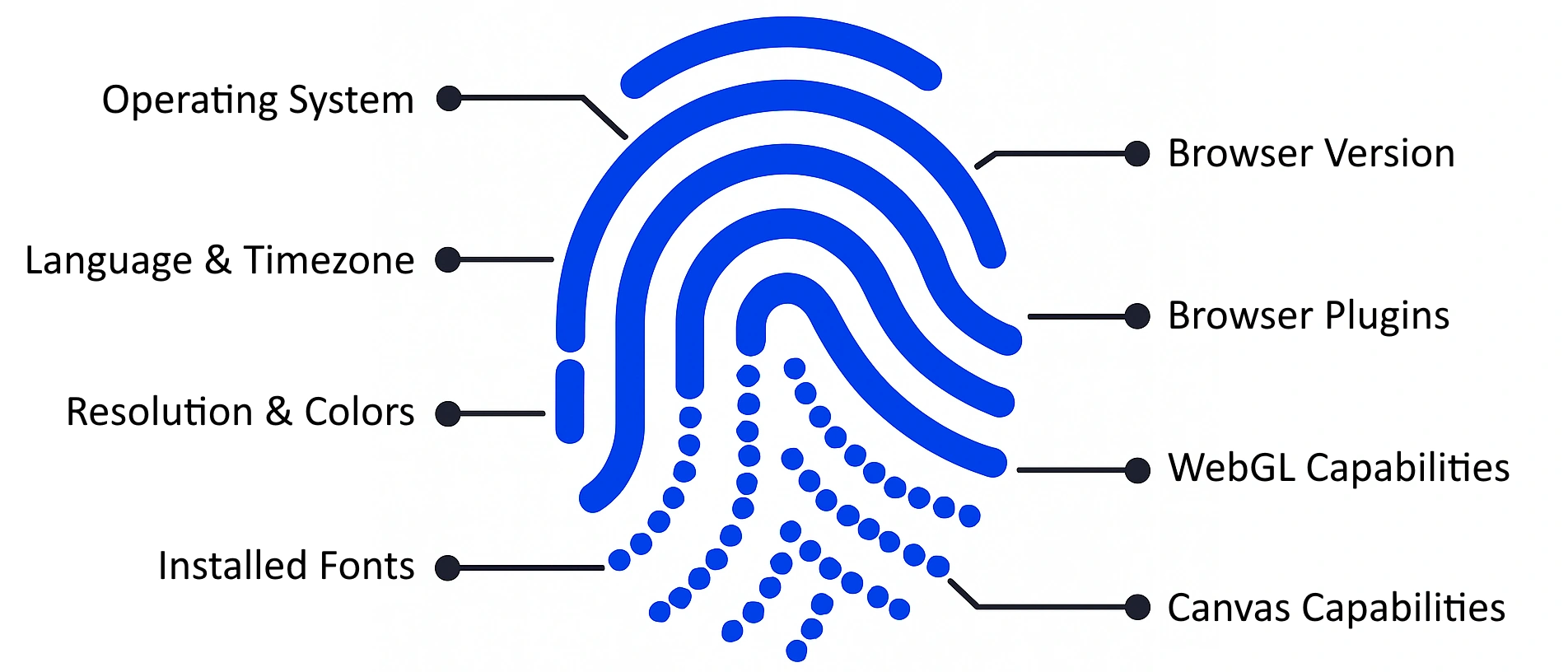
For example, here is some data about your current browser:
| Your Fingerprint ID | |
| Browser User Agent | |
| Browser Version | |
| Operating System | |
| Screen Resolution | |
| Screen Colors | |
| Device Locale | |
| Device Language | |
| Device Timezone | |
| Browser Plugins | |
| Browser Extensions | |
| System Fonts |
https://fingerprint.squidproxies.com
IP Fingerprint Databases
Various organizations also maintain extensive databases to link IP addresses to households – including linking IP addresses to names, addresses, phone numbers, and social media profiles – for marketing, legal, and law enforcement purposes.
Some examples of such databases include:
| Advanced IP Databases | Description |
| El Toro's IP+ Targeting DB | El Toro's patented algorithm provides marketers with accurate, traceable and transparent targeting that matches IP addresses to precise household addresses… with up to a "95% confidence level". |
| Palantir's Gotham DB | Palantir's Gotham database aggregates billions of records, including IP addresses from ISP subscriber records to individuals, addresses, phone numbers, and social security numbers, for law enforcement and intelligence purposes. |
| Oracle's BlueKai | Oracle's BlueKai platform collects and aggregates user data, including IP addresses, to build detailed consumer profiles for targeted advertising. This data encompasses browsing behavior, purchase history, and demographic information. |
| Tapad's Device Graph | Tapad (owned by Experian) links IP addresses and device identifiers to identify and target consumers across multiple devices within a household. This facilitates consistent messaging and measurement across platforms. |
| NSA's XKeyscore | The NSA's XKeyscore program collects and analyzes global internet data, including IP addresses, to identify and monitor individuals' online activities for intelligence purposes. It allows analysts to search and retrieve vast amounts of digital communications. |
| GCHQ's Karma Police | The UK's GCHQ operated the Karma Police program to collect IP addresses and web browsing histories, aiming to build profiles of internet users for surveillance and intelligence gathering. |
| Russia's SORM | Russia's System for Operative Investigative Activities (SORM) mandates ISPs to provide the Federal Security Service (FSB) with access to users' communications, including IP addresses, for surveillance and monitoring purposes. |
Proxy Benefits
Benefits of Using Proxies
Proxies are versatile tools that can come with a variety of benefits for web browser:
- Proxies Can Keep You Anonymous
A properly configured anonymous proxy server would mask your underlying IP address while only exposing the proxy server's IP address to the broader internet, making it significantly harder for websites and advertisers to track your online activities and build a profile linked to your actual identity. - Proxies Can Protect Your Security
While any internet-connected device must be secured independently, proxies potentially help as an additional layer of defence against potential cyber attacks. For example, a Denial of Service attack associated with your browsing activity behind an anonymous proxy would only be able to target the proxy's IP address rather than your personal IP address. - Proxies Can Customize Your Location
Connecting through an anonymous proxy server in a different geographic location allows you to access content as if you were browsing from that region. This can be valuable for accessing content designed for a specific country or region without physically traveling to that location. - Proxies Can Multiply Your Presence
Typically, Internet service providers only allocate a single IP address for all activity performed under a single connection. Proxies can also allow your business to operate numerous online personas across a pool of independent proxy IP addresses. - Proxies Can Automate Your Activity
All browsing activity from a single IP address is often limited by websites to what could be done manually by a single person. Hence, proxies are often critical for automating data collection and other browsing, enabling automations to run simultaneously at a much larger scale.
Popular Use Cases For Proxies
Proxies are versatile tools, supporting a wide variety of business use cases.
| Use Case | Description |
| Secure Browsing | Protect your online identity and sensitive data by masking your IP address through a secure proxy network. |
| Web Scraping | Collect public web data efficiently at scale with high-performance proxies optimized for data extraction. |
| Web Marketing | Verify ad placements, manage multiple accounts, and conduct location-based testing for marketing campaigns. |
| Market Research | Access localized content and pricing information from anywhere in the world to inform your business strategy. |
| Competitive Intelligence | Monitor competitor websites, pricing, and marketing strategies from different geographic locations. |
| Dynamic Pricing | Track market price fluctuations in real-time across different regions to optimize your pricing strategy. |
| Cyber Security | Test your security infrastructure and identify vulnerabilities by simulating attacks from multiple IP addresses. |
| Brand Monitoring | Monitor how your brand appears across different markets and identify unauthorized use of your brand assets. |
| Copyright Protection | Scan the web for unauthorized distribution of your copyrighted materials and protect your intellectual property. |
Popular Industries For Proxies
Proxies can be used across various industries to collect valuable data and insights.
| Industry | Description |
| Data for AI | Train and validate machine learning models with high-quality web data collected through a proxy network. |
| Data for SEO | Monitor search rankings across different locations and devices to optimize your SEO strategy. |
| Data for ECommerce | Track competitor pricing, product availability, and market trends to stay competitive in your market. |
| Data for Real Estate | Gather property listings, pricing trends, and market data from multiple sources to make informed decisions. |
| Data for Finance | Access market data, financial information, and investment insights from multiple geographical locations. |
| Data for Travel | Monitor flight prices, hotel rates, and travel deals across different regions to optimize your offerings. |
| Data for HealthCare | Gather medical research, healthcare trends, and industry data to drive innovation and improvements. |
| Data for Telecommunications | Monitor service quality, market coverage, and competitor offerings across different regions. |
| Data for Government | Access public records, regulatory information, and compliance data from multiple jurisdictions. |
Proxy Types
Finding proxies online can be a confusing experience because there are so many different types of proxies advertised. Let's break down all the different proxy types here:
Proxies By Protocol
Proxies By Anonymity
Proxies By Quality
Proxies By Purpose
Proxies By IP Source
Proxies By IP Rotation
Proxy Types: By Protocol
Proxies can be categorized based on the network protocol used to route traffic between your device and the Internet. The choice of protocol determines how a proxy interacts with your internet connection, the amount of data processed, and the types of applications supported:
| Proxy Type | Description |
| Web Proxies | Web proxies are typically free, ad-supported web-based applications that allow you to load URLs directly on their website. Ideal for bypassing basic web filters at a school or office. |
| HTTP Proxies | HTTP proxies are servers configured within your browser (or other applications) for handling all HTTP and HTTPS traffic. Ideal for a robust browsing experience, web scraping, and most proxy use cases. |
| Socks Proxies | Socks proxies operate at a lower networking level with support for proxying additional applications. Ideal for P2P applications like torrenting and games, but slower than HTTP proxies for web browsing. |
| Virtual Private Networks | Virtual Private Networks (or VPNs) encrypt all internet traffic system-wide, routing it through a secure tunnel to a remote VPN server. Ideal for system-wide privacy but may slow connection due to encryption. |
Proxy Types: By Anonymity
Proxies can be classified by the level of anonymity they provide. This determines how much of your real IP address and proxy usage is visible to the websites you visit—ranging from transparent forwarding to complete masking of identity and intent.
| Proxy Type | Description |
| Transparent Proxies | Transparent proxies are open servers that forward the original IP and show proxy use to websites. Ideal for caching, monitoring, and basic access control. |
| Distorting Proxies | Distorting proxies send a fake IP address but still reveal proxy use to the destination. Ideal for accessing region-blocked content with light privacy. |
| Anonymous Proxies | Anonymous proxies mask the real IP address but indicate proxy usage to the server. Ideal for bypassing geo-blocks with standard privacy needs. |
| High-Anonymity Proxies | High-anonymity proxies hide both the IP address and any trace of proxy use. Ideal for stealth operations, secure scraping, and sensitive browsing. |
Proxy Types: By Quality
Proxies vary in reliability, speed, and exclusivity. This classification helps users choose between free, shared, or dedicated options based on performance needs and risk tolerance for the intended task.
| Proxy Type | Description |
| Public Proxies | Public proxies are free-to-use servers with minimal security and poor reliability. Commonly used for bypassing simple blocks on low-risk tasks. |
| Shared Proxies | Shared proxies are IP addresses distributed among multiple users to reduce cost. Suitable for low-sensitivity browsing, scraping, and testing. |
| Semi-Dedicated Proxies | Semi-dedicated proxies are limited to a few users for improved speed and stability. Recommended for mid-level tasks requiring better reliability. |
| Dedicated Proxies | Dedicated proxies are exclusive IP addresses assigned to one user for full control and performance. Best suited for automation, account access, and high-throughput operations. |
Proxy Types: By Purpose
Proxies are often specialized for particular use cases. This category highlights how proxies can be configured for tasks like content caching, traffic filtering, automated data scraping, or location-based access:
| Proxy Type | Description |
| Caching Proxies | Caching proxies store requested web content temporarily to reduce load times and server strain. Best used for speeding up repeat visits to the same sites. |
| Filtering Proxies | Filtering proxies scan and control traffic based on custom rules, such as blocking or modifying specific requests. Commonly applied in schools, offices, and parental control systems. |
| Scraping Proxies | Scraping proxies route automated requests through rotating IPs to avoid detection and limits. Often used in large-scale data gathering projects that require stealth. |
| Geographic Proxies | Geographic proxies channel traffic through servers in chosen regions to change location visibility. Useful for unlocking geo-blocked content or testing localized experiences. |
Proxy Types: By IP Source
The source of a proxy's IP address influences its trust level and detection risk. Proxies can come from datacenters, home ISPs, or mobile networks—each offering different balances of authenticity, speed, and resilience.
| Proxy Type | Description |
| Datacenter Proxies | Datacenter proxies are hosted on high-performance servers from commercial data centers, without ties to ISPs or home users. Best used for speed-focused tasks but more likely to be flagged due to their synthetic origin. |
| Residential Proxies | Residential proxies route traffic through real IP addresses assigned by internet providers to households. Frequently used for stealth browsing and scraping that mimics regular human behavior. |
| Residential ISP Proxies | Residential ISP proxies combine datacenter infrastructure with IP addresses registered as residential by ISPs. Designed to deliver both authenticity and consistent uptime. |
| Residential Mobile Proxies | Residential mobile proxies rely on IP addresses assigned to phones and tablets via cellular networks like 3G, 4G, or 5G. Commonly used in high-risk environments where maximum undetectability is required. |
Proxy Types: By IP Rotation
IP rotation determines how often a proxy changes the IP address assigned to your session. This classification contrasts stable static proxies with dynamic rotating ones, useful for different levels of automation, session control, and block avoidance.
| Proxy Type | Description |
| Static Proxies | Static proxies provide a fixed IP address that remains the same across sessions and requests. Often used for account logins, ad verification, and session-based activities. |
| Rotating Proxies | Rotating proxies assign a new IP address at set intervals or per request by pulling from a pool of IPs. Commonly used for high-volume scraping, automation, and bypassing rate limits. |
Proxy Providers
Web Proxy Providers
There's a plethora of browser-based proxy providers hosting free ad-supported web proxy service, typically for casual personal use:
| Provider | Features | Pricing |
| ProxySite |
| Free: Ad-supported |
| CroxyProxy |
| Free: Ad-supported / $3.50/month: Premium |
| KProxy |
| Free: Ad-supported / $10/month: Premium |
Last updated: May 21, 2025
Public Proxy Lists
As discussed above, public proxies allow for open access without authentication, and there are providers that help organize public proxy lists.
| Resource | Features | Pricing |
| ProxyNova |
| Free: Ad-supported |
| FreeProxyWorld |
| Free: Ad-supported |
| Proxy-List.download |
| Free: Ad-supported |
| Spys.One |
| Free: Ad-supported |
| FreeProxy.cz |
| Free: Ad-supported |
| PremProxy |
| Free: Ad-supported |
Last updated: May 21, 2025
Datacenter Providers
The following proxy providers offer datacenter proxies, which are the most efficient and reliable for the majority of proxy use cases:
| Provider | Features | 100 Shared Proxies | 100 Dedicated Proxies |
| BrightData |
| $100/month | $170/month |
| OxyLabs |
| $100/month | $155/month |
| SmartProxy / Decodo |
| $3.50/month | $145/month |
| Webshare.io |
| $2.99/month | $119/month |
| IPRoyal |
| n/a | $157/month |
| ProxySeller |
| n/a | $153/month |
| ProxyCheap |
| n/a | $199/month |
| Infatica.io |
| $0.43/GB for 350GB | $150/month |
| PrivateProxy |
| n/a | $180/month |
Last updated: May 29, 2025
Residential Providers
The following proxy providers offer residential proxies, which offer the highest success rates for restrictive websites:
| Provider | Features | Residential Proxies @ 300GB+ |
| BrightData |
| $3.78/GB |
| OxyLabs |
| $2.75/GB |
| Evomi |
| $2.80/GB |
| SmartProxy / Decodo |
| $1.75/GB |
| Webshare.io |
| $1.75/GB |
| IPRoyal |
| $2.45/GB |
| LunaProxy |
| $1.18/GB |
| Geonode |
| $0.75/GB |
| ProxyRack |
| $2.50/GB |
| DataImpulse |
| $1/GB |
Last updated: May 30, 2025